You may not know what auditing is or how it applies to you, but you should. Auditing is the process of systematically examining and reviewing an entity’s accounts and records so as to verify their accuracy, reliability, legitimacy, and completeness. It has evolved over time into a procedure that every company needs to do in order to maintain compliance with regulations like the Sarbanes-Oxley (SOX) Act passed by Congress on July 30th 2002.
The Audit Checklist for Cloud Compliance provides an easy way for your organization to get started on this vital task—and make sure all your cloud computing activities are safe from scrutiny by regulators who want transparency of data ownership and access.
- What is Cloud Computing?
- What are the benefits of cloud computing?
- Why do we need a cloud computing audit?
- What is SOX 404?
- What is the role of audit in cloud computing?
- How is cloud computing useful in auditing?
- What is compliance in cloud computing?
- What is auditing in cloud computing?
- Why do companies need a cloud services audit?
- What are the different audits performed by cloud auditors?
- What deliverables are produced from a cloud audit?
- What are the security auditing issues in cloud computing systems?
- What are the 6 common cloud provider security issues?
- In conclusion cloud security & cloud service providers
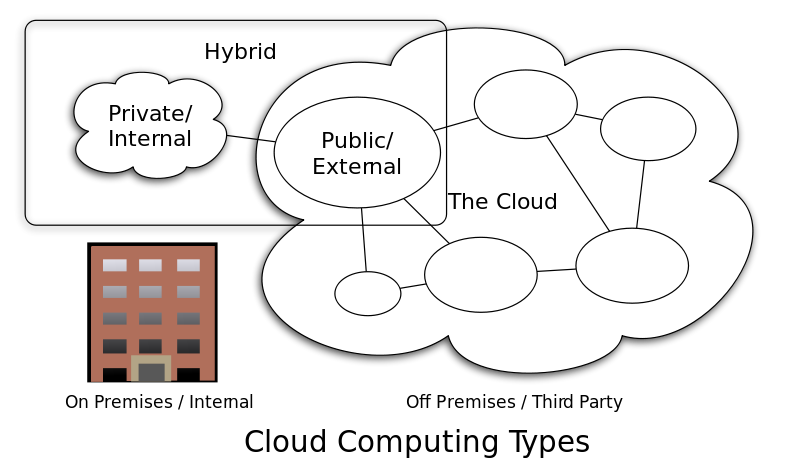
What is Cloud Computing?
Traditional computing can be defined as computers being used by people to do things. That sounds easy enough, but what about cloud computing? The term “cloud” has become a catch-all phrase for describing software and hardware solutions that are not on-site. This means you access your applications via the Internet, which is designed to be a secure, private cloud network. If you have a smartphone or own a computer that’s connected to the Internet at home, chances are that you’re already using cloud computing services without even knowing it!
Some examples of data being stored in “the cloud” include server backups, files, emails, and databases. The advantage of these solutions is that you don’t need to worry about having a ton of storage space on your hard drive. This, in turn, saves companies money by not having them pay for servers or maintenance.
What are the benefits of cloud computing?
First of all, if you want to understand an audit of cloud computing you must first understand the benefits of using the cloud. They may seem obvious, but here are a few:
1. Seamlessly scale up/down services as demand requires;
2. Eliminate capex spending on hardware;
3. Pay for what you use (vs. having to buy the whole farm);
4. Improve business efficiency by enabling workload consolidation;
5. Increase/decrease resources as business needs change;
6. Centralize all data and applications in a single location, which reduces IT complexities and costs;
7. Securely store data remotely – it is therefore available anytime, from anywhere.
While these are some of the most obvious, there are many more which will be revealed throughout this post.
Why do we need a cloud computing audit?
The primary goal of a Private Cloud Audit Checklist is to ensure that all data requests, access, processing, and storage are properly documented for regulatory compliance. Security controls also demand evidence of periodic cloud audits which confirm these procedures are effective. This process should help avoid problems that occur at companies that use cloud services without the proper internal controls in place.
A secondary goal of this Cloud Audit Checklist is to establish a process that will allow an auditor to document compliance with the security standards required by law or regulation. The checklist can also be used for security incidents-related SOX 404 audits, thus helping financial institutions prove they have adequate controls in place to protect customer data.
What is SOX 404?
SOX 404 requires public companies to prove that material financial transactions are legitimate, accurate, and documented. This requirement has led organizations to seek out ways of demonstrating that critical internal control procedures are effective, especially in the area of protecting online access. The use of cloud services without the proper internal controls is believed to have caused the loss of customer data at some companies that used cloud without adequate control.
SOX 404 compliance can be achieved through a combination of traditional and cloud solution controls, which rely on applying security policies to all information systems and employees. The use of public/private clouds/hybrid clouds will also most likely require changes to existing policies and procedures.
Audit facilitates risk mitigation that enables organizations to realize business benefits from moving to the cloud.
What is the role of audit in cloud computing?
Now, what is the role of audit in cloud computing? As enterprises are gearing up to adopt cloud services, they have to ensure that their internal controls are in place. Audit plays an integral role in ensuring the effectiveness of these internal controls, and thereby facilitates risk mitigation that enables organizations to realize business benefits from moving to the cloud.
Typically this begins with an organization’s internal audit department for assessing the risks of adopting cloud in their own organization. Internal auditors in an enterprise evaluate how well documented, implemented, and enforced its policies are for security, privacy, and quality of service in auditing cycles which are followed by identifying the gaps/deficiencies that may impede the effective adoption of cloud services.
Meanwhile, external auditors hired by cloud service providers (CSPs) also assess an organization’s risk posture when it subscribes to cloud services. They follow standard criteria while performing this assessment to arrive at objective conclusions regarding the risks associated with using CSPs’ services. These assessments are primarily based on auditing of controls like security, availability/elasticity, resiliency, etc., which are integrated into these cloud services. As CSPs keep updating the security features/controls in their cloud service portfolios periodically, external auditors have to ensure that these controls are effective both for the current as well future needs of their client organizations.
How is cloud computing useful in auditing?
The need for companies to have a reliable technology infrastructure to run their businesses means that auditors must have access to information about cloud computing, especially when it comes to the accounting and reporting of costs. Using a cloud service provider will give an auditor a high degree of transparency into how data is collected and processed, but understanding how this works requires time and effort.
In addition, auditors need to understand the impact of cloud computing on their financial statements and disclosures, as well as other accounting issues that can arise from using a service provider.
As the industry continues to grow, there will be greater possibilities for fraud and theft in an environment where data is shared between multiple providers without proper understanding.
What is compliance in cloud computing?
Compliance refers to the act of adhering to or following rules. In other words, it is when someone follows something they are supposed to do, like safety procedures in the workplace. So compliance in cloud computing internal audits refers to the acts of following certain rules that are set out for cloud computing. Some of these rules include:
Cloud management and security audits: Auditing and reviewing the cloud infrastructure and processes for compliance with internal policies and industry standards. This involves auditors logging into your system, verifying that only authorized users have access to the system and that it is secure from external threats.
- Compliance enforcement: The act of enforcing the compliance rules, which involve righting or putting things back into place.
- Another would be to take corrective actions when non-compliance is identified.
- Cloud computing training: This ensures that users understand how to use a cloud system and comply with company policy.
What is auditing in cloud computing?
Auditing is essentially the action of making sure someone complies with a rule or follows safety procedures. Auditors are very important in this sense because they make sure people, no matter where they are working from – not just at the office, follow certain safety procedures.
Why do companies need a cloud services audit?
There are many reasons why one would want to do cloud audits. For example, companies do it to ensure that data integrity is maintained. This can help them avoid unexpected expenses and any cybercrime that might occur in the cloud environment. Other reasons for auditing cloud servers may include that a company wants to look over its processes and systems and make sure they are up-to-date.
What are the different audits performed by cloud auditors?
There are many different audits an auditor can perform on cloud systems. The most common ones are:
Performance audit: An authorized auditor tests the cloud system to determine if it is meeting minimum performance levels established by the client’s security controls policy. Performance audits are performed by the client, not the service provider. However, auditors are able to test the service providers’ controls at their discretion.
Security audit: The Cloud auditor ensures that all controls are designed to effectively protect client data and systems. Security audits are performed by the client, however, some service providers will provide self-assessments on their own controls for your review.
Configuration audit: The cloud auditor ensures that all configured components of the cloud system meet security requirements defined by the client’s security policy. Configuration audits test whether a provider is complying with the security concerns set forth by the customer. Configuration audits are performed by both parties, but they are most commonly performed by the cloud provider.
Systems Management Audit: Auditors verify that systems management controls are designed to achieve stated objectives for availability of services, reporting of incidents, data recovery processes, etc. Systems Management Audits are performed by the client, however, service providers will provide self-assessments on their own controls for your review.
Legal and regulatory compliance audit: The cloud auditor ensures that all components of the system are compliant with applicable laws or regulations. Legal audits are typically only performed by the client unless auditors have specific knowledge in a certain area. For example, an auditor may test for HIPAA compliance if that is a requirement of the client.
Business continuity audit: The cloud auditor ensures that the client’s business continuity plans and procedures are appropriate and meet stated objectives. Business Continuity Audits are performed by both parties, but they are most commonly performed by the cloud provider.
Marketing claims audit: An auditor tests marketing claims to ensure that they can be confirmed or denied. This is done by requesting documentation from the service provider and reviewing it for accuracy. Marketing audits are performed by both parties, but they are most commonly performed by the cloud provider.
Service Level Agreement (SLA) audit: The auditor ensures that all components of the system meet specifications outlined in the customer’s Service Level Agreement. SLA audits are performed by both parties, but they are most commonly performed by the cloud provider.
Privacy Protection audit: The auditor ensures that all components of the system comply with customer privacy requirements as stated in their information security policy and Service Level Agreement (SLA). Privacy audits are typically only performed by the client unless auditors have specific knowledge in a certain area. For example, an auditor may test for HIPAA compliance if that is a requirement of the client.
Change management audit: The cloud auditor ensures that all changes to the system are logged and accounted for appropriately according to stated policies. Change Management Audits are performed by both parties, but they are most commonly performed by the cloud provider.
Documentation audit: The auditor ensures that all documentation is up to date with regard to the system design, configuration, policy requirements, etc. Documentation audits are typically only performed by the client unless auditors have specific knowledge in a certain area. For example, an auditor may test for HIPAA compliance if that is a requirement of the client.
Data security audit: The auditor ensures that data security requirements as stated in the customer’s security policy and Service Level Agreement (SLA) are met. Data Security audits are typically only performed by the client unless auditors have specific knowledge in a certain area. For example, an auditor may test for HIPAA compliance if that is a requirement of the client.
Logical and physical access audit: The auditor ensures that logical and physical controls for user access in the system comply with stated requirements. Logical and Physical Access Audits are typically only performed by the client unless auditors have specific knowledge in a certain area.
Testing controls: Controls such as Business Continuity Plans (BCPs), Disaster Recovery Plans (DRPs), and security policies are tested to determine how well they work in practice via drills and exercises. Control testing audits are performed by both parties, but they are most commonly performed by the cloud provider.
Testing security configuration: Security settings are tested to determine how well they work in practice via drills and exercises. Testing audits are performed by both parties, but they are most commonly performed by the cloud provider.
Infrastructure audit: The auditor ensures that all components of the system comply with customer requirements as stated in their security policy and Service Level Agreement (SLA). Infrastructure audits are typically only performed by the client unless auditors have specific knowledge in a certain area. For example, an auditor may test for HIPAA compliance if that is a requirement of the client.
It is important to understand that cloud computing systems introduce a number of risks that are not present in the same way in an analogue system.
What deliverables are produced from a cloud audit?
A list of findings is produced from audit activities, which are items that are not in compliance with the security policy or SLA. Typically, findings are categorized as
- Severity 1, which has a direct impact on the security or privacy of data; or
- Severity 2, which has an indirect impact on the security or privacy of data.
After findings are produced, they must be prioritized for corrective action based on risk to the organization. The auditor then prepares a final report that summarizes the findings and recommended courses of action. The report is typically distributed to the client and the cloud provider, after which corrective actions are implemented by both parties.
Other deliverables that may be produced from a cloud audit are conclusions, recommendations for security threats enhancement, etcetera. These are commonly only used by auditors for their own purposes or to pass on to other auditors/managers.
What are the security auditing issues in cloud computing systems?
It is important to understand that cloud computing systems introduce a number of risks that are not present in the same way in an analog system. Firstly, the service provider has complete control of the infrastructure. Secondly, the data is stored over a number of servers in multiple physical locations. Thirdly, access to services by outside parties may be controlled either directly or via other services that the supplier provides. Fourthly, cloud services can be accessed from anywhere in the world, at any time or at all times.
What are the 6 common cloud provider security issues?
- Slipping through the cracks: This refers to the risk that a security vulnerability exists but is not identified by the cloud service provider. A good analogy would be a house with a faulty lock on its front door – someone could easily break in without anyone noticing. However, one reason this type of attack is unlikely is because of the rigorous testing that is typically carried out by the service-provider interaction.
- Security by obscurity: This refers to when an attacker can gain access to information via a backdoor or another previously unknown route. For example, if the security company uses SMS verification for authentication, they may send passwords/one-time codes in plaintext over insecure networks such as 3G. Attackers could access this information, even if the attacker didn’t know the password.
- Someone has your password: This refers to when an attacker can gain access to a customer’s account without knowing the username or password. An example of this would be an email phishing scam where attackers take control of victim’s accounts by gaining access to their passwords – either through social engineering or by using brute force methods. The attacker could then use the account to send spam, damage the customers’ data (e.g. delete files/backups), or cause other types of harm.
- Unauthorized access: This refers to when an unauthorized user gains physical access to sensitive information – e.g. a customer’s backup. For example, if the data center had only one physical security layer (e.g. a locked door) an attacker could potentially break in and access sensitive information that should not be easily accessible.
- Insider threat: This refers to when an employee or other individual with authorized access deliberately damages company assets by accessing them inappropriately. An example of this would be an employee who makes a copy of sensitive company information and sends it to their personal email address.
- Internal security measures: This refers to the security measures that are used within the cloud provider’s own infrastructure to protect sensitive data – e.g. secure communication between servers, controlled access to other users, etc.
In conclusion cloud security & cloud service providers
In conclusion, cloud-based computing provides a considerable amount of convenience through on-demand broad network access which provides flexibility for business owners. But it also has a number of security risks that are not present in an analog system. The extent to which these need to be considered when looking at auditing needs will depend on the type and scale of cloud service being supplied. It will also need to include the cloud deployment models, specific policies, and procedures that have been put in place by the service provider. The bottom line is, that cloud resources can enhance operational effectiveness as long as you do your homework and stay on top of security challenges.

Dean Emerick is a curator on sustainability issues with ESG The Report, an online resource for SMEs and Investment professionals focusing on ESG principles. Their primary goal is to help middle-market companies automate Impact Reporting with ESG Software. Leveraging the power of AI, machine learning, and AWS to transition to a sustainable business model. Serving clients in the United States, Canada, UK, Europe, and the global community. If you want to get started, don’t forget to Get the Checklist! ✅